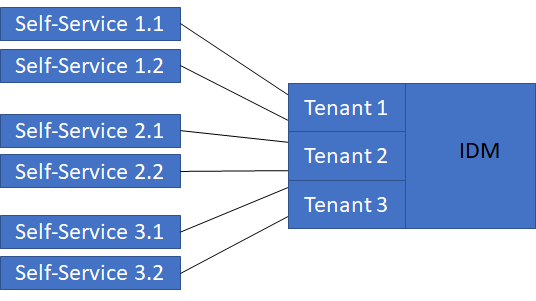
This article describes how to deploy and connect Smart ID Self-Service on a separate server. Smart ID Self-Service can be deployed multiple times in a customer environment for different reasons. One Self-Service instance can only connect to one specific tenant, which is the reason a separate instance per tenant is required. On the other hand, you might want different instances of Smart ID Self-Service in different time zones, or multiple instances per tenant to handle a high load on the system (perhaps behind a load balancer).
Smart ID Self-Service communicates with an Identity Manager Operator instance via a separate internal REST API dedicated only for self-service communication.
Example setup:
<SMARTIDHOME>
In this article, <SMARTIDHOME> refers to /home/nexus, but this can be different depending on the setup.
Step-by-step instruction
Configure URL to Identity Manager Operator - Docker deployment
To set up Smart ID Self-Service on a separate server you need to configure the URL to Identity Manager Operator:
-
Open this file for editing: <SMARTIDHOME>/docker/compose/identitymanager/<admin|operator|tenant>/docker-compose.yml.
-
Enter the URL to Identity Manager Operator in the parameter baseURL. This is the same URL you use when running Identity Manager Operator on the browser. No specific authentication is needed in the configuration. The authentication is done via the JWT created during user authentication. See an example of the configuration below.
Example: docker-compose.yml configuration
- 'APPLICATION_YAML={ "prime": { "baseUrl": "https://${IDM_OPERATOR_DOMAIN_PREFIX}.${SMARTID_INGRESS_DOMAIN}", "tenantId": 1, "instanceId": "selfservice-default-instance" } }'
It is highly recommended to use an HTTPS endpoint as baseURL.
Configure URL to Identity Manager Operator - Legacy deployment
-
Open this file for editing: /tomcat/webapps/selfservice/WEB-INF/classes/application.yaml.
-
Enter the URL to Identity Manager Operator in the parameter baseURL. This is the same URL you use when running Identity Manager Operator on the browser. No specific authentication is needed in the configuration. The authentication is done via the JWT created during user authentication. See an example of the configuration below.
Example: application.yaml (war file) configuration
prime.tenantId: To which tenant should the USSP be connected prime.instanceId: A unique name of the ussp instance. prime: tenantId: 1 instanceId: selfservice-default-instance baseUrl: https://myIDMhost:8444/idm-operator
It is highly recommended to use an HTTPS endpoint as baseURL.
Additional information
