This article describes the support for the Certificate Management Protocol (CMP) in Smart ID Certificate Manager via Protocol Gateway.
Certificate Manager supports certificate enrollment over the Certificate Management Protocol (CMP), which is an Internet protocol used for obtaining X.509 digital certificates in a public key infrastructure (PKI). CMP is defined in RFC 4210.
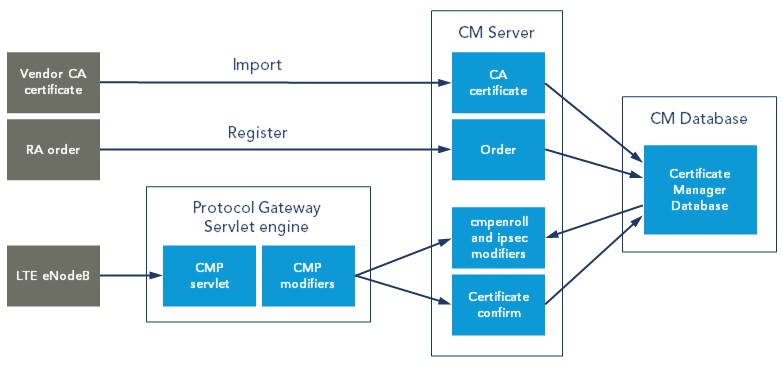
The Protocol Gateway CMP service is compliant with the Certificate Enrollment Protocol (CMP) v2 as profiled by 3GPP for LTE, see 3GPP TS 33.310 version 9.5.0, and supports both initial enrollment requests and update requests for certificate renewal.
Request certificate via CMP and Protocol Gateway
The enrollment process is made up of the following major steps:
-
Hardware registration
-
If certificate-based signature is to be used, the vendor CA certificate must be imported to CM with the Administrator's workbench (AWB).
In the AWB client, select Cross menu and Import Certificate and open the file that contains the vendor CA certificate. See Import external CA certificate in Certificate Manager. -
If a password-based mac is to be used, it must be enabled in the
cmpenrollcertificate format.
In the file cmpenroll.conf, setenroll.messagesigner.hmac.enabledtotrue. For information on settings in cmp.conf, see also CMP security configuration in Certificate Manager. -
The hardware must be registered in the Certificate Manager database, via the Registration Authority (RA) in Certificate Manager, in the Order tab. The registration shall contain the fully qualified domain name (FQDN).
-
-
Certificate enrollment
-
A certificate request is sent from the LTE eNodeB or Security Gateway via the CMP service to the Certificate Factory.
-
The request must contain the FQDN and must be signed either with a vendor device certificate, the old device certificate or a password-based mac. The FQDN is verified against the registrations in the database. The CMP request signature is verified and if it is signed with a certificate then the signature certificate is verified, and must be issued by a CA in the Certificate Manager database.
-
If the request meets all requirements, a certificate will be created and returned to the requesting hardware.
-
