This article is valid for Smart ID 21.10 and later and Digital Access 6.1.0 and later.
This article describes how to deploy the Smart ID Digital Access component on Red Hat Enterprise Linux (RHEL) 8 using Ansible and Podman.
Prerequsites
-
A VM which will be a control RHEL 8 system with ansible version 2.0 or above for running the ansible playbook.
Make sure that containers.podman is installed. If not, run this command:ansible-galaxy collection install -f containers.podman -
Target systems should have RHEL 8 with podman installed on it.
-
Enable SSH communication between controlling VM and target systems (Check ssh using the key)
-
The UDP ports shall be open to traffic of each of authentication method servers. You can locate these ports in Digital Access Admin under Manage System > Authentication Methods for each added Authentication method.
-
External Database setup
-
ansible_DA.tgz
Step-by-step instructions
Set up Ansible playbook
-
Copy and extract ansible_DA.tgz file on the controlling VM.
-
Before running the playbook:
-
Add the target host IPs in the inventory file present inside the ansible folder depending on the distribution of DA services.
-
If you want to setup Digital Access configuration from the beginning, then copy the config folder which is inside the ansible folder on the control system.
For HA mode: change LocalConfiguration.xml of the service (Policy, Authentication, Distribution, Access Point) and replace "Administration service" mHost to Host's IP of Digital Access where administration service will be running.Snippet from LocalConfiguration.xml
<node> <object key="c000ejp1m5" name="Administration Service" trans="ivjq0838gkxs" ver="50600"> <attribute name="mAllInterfaces" type="boolean" value="false"/> <attribute name="mPort" type="integer" value="8300"/> <attribute name="mHost" type="string" value="198.160.x.x"/> <attribute name="mType" type="integer" value="5"/> <attribute name="mId" type="integer" value="1"/> </object> -
By default, the playbook reads the config folder in the */ansible/ folder and the images of DA services in the */ansible/images folder.
-
-
Change the current working directory to ansible in the terminal.
Change working directory
cd ansible -
Run the ansible playbook using this command:
Run ansible playbook
ansible-playbook -i inventory <yml_file_name> --ask-become-pass -
It will ask for root password and then execute the playbook.
-
If the setup is successful, it should show a status as the below screenshot. Make sure it shows 0 in the failed and unreachable values.
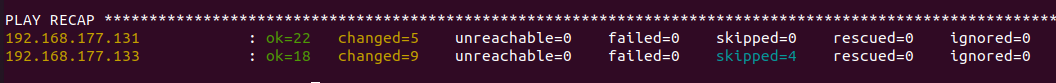
Set up Digital Access
-
Log in to Digital Access Admin with an administrator account.
-
Change the Administration Service internal host from "admin" to machine public IP for HA mode.
-
Connect to the HAG, OATH, OAUTH and Reporting databases as mentioned here - Configure all databases in Digital Access.
-
If the services can not listen on 0.0.0.0:8090, then restart the services.
Instructions for High Availability
Prerequisites
-
Databases are available and connected.
-
Multiple Digital Access component are running. in the examples in this article they are called DA-1, DA-2, DA-3, and DA-4:
-
Only one Administration service is installed. This is done on DA-1.
-
-
The IP addresses of all four nodes must be known.
Change hosts and add services
-
Log in to Digital Access Admin with an administrator account.
-
Change the host of all the registered services.
-
Add new Services for DA-2/ DA-3/DA-4.
Change the host of registered Policy service:
-
In Digital Access Admin of DA-1, go to Manage System > Policy Services.
-
Select the registered Policy Service.
-
Change the Internal Host from 127.0.0.1 to DA-1's IP Address.
-
Check Distribute key files automatically.
-
Click Save.
Add new services
-
In Digital Access Admin of DA-1, go to Manage System > Policy Services.
-
Click Add Policy Service…
-
In Display Name enter "Policy Service 2".
-
In Internal Host enter the IP address of DA-2.
-
Check Distribute key files automatically.
-
Select the Server Certificate and Add it.
-
Note down the Service ID of newly added Policy Service. This is used as mID in later steps
Set up services
There will be only one administration service running at DA-1, so all other Digital Access instances need to have administration service at disabled state.
-
Stop the administration service of the other Digital Access instances.
Stop service
sudo podman stop admin -
Change serviceId of services of the other Digital Access instances:
-
Open LocalConfiguration.xml (opt/nexus/config/<service>/config/LocalConfiguration.xml)
-
Search for the
<service>section -
Replace mID with the new mID:
<?xml version="1.0" encoding="UTF-8"?><com> <portwise> <core> <id>3</id> </core> <policy> <node> <object key="c000ejp1m5" name="Administration Service" trans="s4x1qgx4q5fk" ver="50600"> <attribute name="mAllInterfaces" type="boolean" value="false"/> <attribute name="mPort" type="integer" value="8300"/> <attribute name="mHost" type="string" value="10.0.0.10"/> <attribute name="mType" type="integer" value="5"/> <attribute name="mId" type="integer" value="1"/> </object> <object key="5t02k8rn7jwg" name="Policy Service" trans="t4x6zmbhkjr4" ver="50600"> <attribute name="mAllInterfaces" type="boolean" value="false"/> <attribute name="mPort" type="integer" value="8301"/> <attribute name="mHost" type="string" value="10.0.0.10"/> <attribute name="mHTTPLogSettings" type="container" value="logsettings"> <attribute name="mEventLogLevel" type="string" value="OFF"/> <attribute name="mLocalCount" type="integer" value="2"/> <attribute name="mAuthenticationTiming" type="boolean" value="false"/> <attribute name="mFileLogLevel" type="string" value="OFF"/> <attribute name="mFileSizeRotationEnabled" type="boolean" value="true"/> <attribute name="mCentralLimit" type="integer" value="15000000"/> <attribute name="mLocalLimit" type="integer" value="5000000"/> <attribute name="mDateRotationEnabled" type="boolean" value="false"/> <attribute name="mCentralCount" type="integer" value="5"/> </attribute> <attribute name="mType" type="integer" value="1"/> <attribute name="mId" type="integer" value="3"/> <attribute name="mK8sServiceHost" type="string" value=""/> </object> </node> </policy> </portwise> </com>
-
-
Restart all services.
Restart services
sudo podman restart <service>
Check setup
-
Start all the required services.
-
Publish the configuration.
-
Check that all services are connected.
-
Do a login to the portal and check if all works as expected and that you can see the portal items and display names properly.
-
In case of any failure, check if sha1sum of shared.key and internal.key for all connected services are the same. The keys can be found under /opt/nexus/config/<service>/keys/.
-
Inspect logs and address any unexpected errors.
Set up load balancer
To set up high availability for Digital Access component, an external load balancer must be used. In this example, we use HAProxy.
-
Log in to Digital Access Admin of DA-1 with an administrator account.
-
In Digital Access Admin, go to Manage System > Access Points.
-
For each added access point:
-
Add a listener by clicking Add Additional Listener…
-
In Host, enter the IP address of the Access Point. Enter a Port, and set Type to Load Balance.
-
Click Add.
-
-
Go to Manage System > Access Points.
-
Select Configure Load Balancing…
-
Check Enable multi-host sessions and Send sticky cookies. Enter a Name of Sticky Cookie to be used by the load balancer service.
-
Click Save.
-
Select Configure Load Balancing…
-
Click Add Pair of Mirrored Access Points...
-
Select Access Point 1 and Access Point 2 as Primary and Secondary server.
-
Click Save.
Configure external storage for logging
-
Mount external storage on host linux machine on mount path /mnt/<some directory> and change its permission to pwuser:root.
-
Write the mapping of the volume mount in the docker-compose.yml file under volumes for admin.
[*For Ansible and Podman, write the mapping of the volume mount in the /ansible/roles/podman_deploy_da/tasks/main.yml]
For example: /mnt/logs:/etc/LogsDir
where /mnt/logs is the external path and /etc/LogsDir is inside the admin container.
-
In Digital Access Admin, go to Monitor system > Logging > Manage Global Logging Settings > Log Directory
-
Enter the <inside container directory path> here. In this case, /etc/LogsDir
-
Publish and restart the Administration service.
