Smart ID Digital Access component can be configured as a High Availability (HA) solution in an active-passive failover scenario. This prevents the system from being unresponsive when one instance, or a certain service, goes down. To enable such a scenario the database needs to be external. How the database HA-setup can look like depends on the corresponding database product in the customer’s environment. See also Set up high availability for Digital Access component.
For HA at least two internal Digital Access component nodes need to be set up and connected. All services could be multiplied except the Administration service. The Administration service is only allowed once and needs to be connected to all other services to publish the configuration. Since the Administration service is not involved in productive tasks, it is not necessary to have this service in HA mode.
It is recommended to have the Access Points (PEP, Policy Enforcement Point) separated from the other Digital Access component services (that is, on a different Digital Access component node) as, in the unlikely case of machine compromise, no sensitive data can be exposed.
Prerequisites for HA
-
At least two internal Digital Access component nodes must be set up and connected
-
The Administration service is only allowed once and must not be duplicated
-
Do not have the Access Point on the same internal Digital Access component node as the other services (to avoid exposure of authorization information)
-
The databases must be external (both user database, OATH and Oauth2 databases)
Load balancing
Digital Access component supports a load balanced scenario as well. In this case a load balancer is configured in front of Digital Access component’s Access Points to spread the load between those services and enable full failover scenario. This setup is recommended for all productive systems.
In an environment with high workload/huge user volumes, one Digital Access component Access Point might be insufficient and potentially would cause system overload or bad reaction times. Therefore, the load is distributed on multiple servers via load balancing.
Example of an HA network
|
In the DMZ |
In the protected network |
|---|---|
|
2 x Access points shall be located in the DMZ or separate network. It is important that the Access points are on a separate network as they must not be on the same machine as the other services. |
2 x internal Digital Access component nodes. Each with Authentication service, Policy service and, if relevant, Distribution service. On one of these Digital Access component nodes, the Administration service should be enabled. |
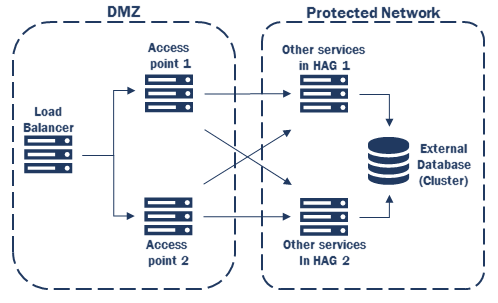
If configured in HA mode, most services of Digital Access component will act as failover scenario. But for the Policy service, internal load balancing is also supported. This means that a certain Access Point (for example, AP1) first talks to its primarily configured Policy service (PS1) and only moves communication to PS2 if PS1 stops responding. Same applies for AP2 and PS2.
