This article describes how to configure Confluence with SAML connection to Smart ID Digital Access component (as Identity Provider).
Prerequisites
A server certificate that will be used for the SAML configuration must be uploaded. An already existing certificate can be used.
Step-by-step instruction
Log in to Digital Access Admin
-
Log in to Digital Access Admin with an administrator account.
Settings in Digital Access
-
In Digital Access Admin, go to Manage Resource Access.
-
Click SAML Federation > Add SAML Federation.
-
In the General Settings tab enter a Display Name. Example: ConfluenceFederation
-
Check Acting as Identity Provider.
-
Uncheck Import metadata automatically.
-
Go to the Export tab.
-
Enter Entity ID. It must be unique among other SAML federations. Example: https://confluencefederation/ipd
-
Leave the API Path as it is.
-
Select a Signing Certificate.
-
Select an Access Point DNS Name.
-
Click Add to save the new federation. We will add an Identity Provider shortly.
-
Go to Confluence to continue the setup.
Settings in Confluence
-
Open the administration interface in Confluence (or JIRA).
-
Select Manage Add-ons and select to install the SAML 2.0 Single Sign-on for Confluence plugin from Bitium.
-
Configure and enter settings like this. The certificate is the certificate used in Digital Access as signing certificate.
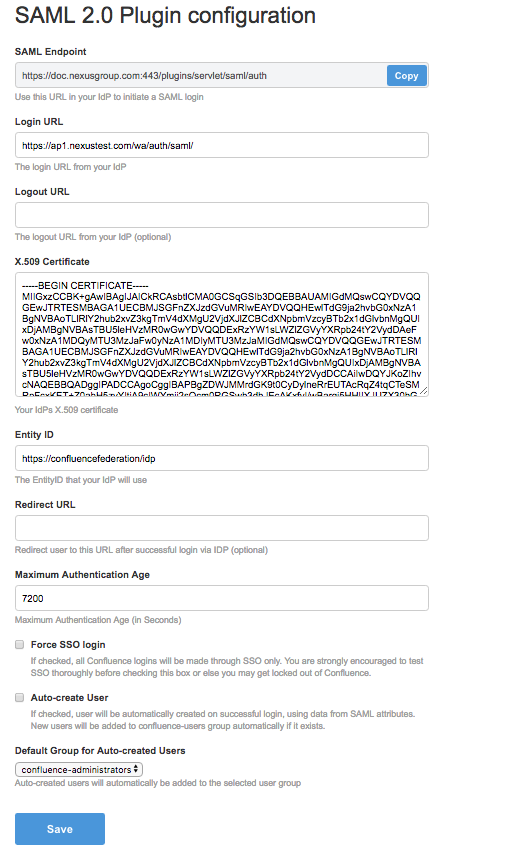
-
Go back to Digital Access Admin and continue the setup.
Continued settings in Digital Access
-
In Digital Access Admin, go to Manage Resource Access.
-
Click SAML Federation and select the newly added SAML federation to edit it.
-
Go to the Role Identity Provider tab and click Add Service Provider.
-
Under Add manually, select SAML 2.0 specification and click Next.
-
Enter a Display Name, a unique name used in the system to identify the service provider (that is, Confluence). Example: MyConfluenceServer
-
Enter Entity ID. This is a unique identifier of the service provider (that is, Confluence). Example: <Url as Confluence knows itself>/confluenceSAML (or jiraSAML)
-
Enter Service Provider URL. This is the value of the topmost field in the Confluence configuration. Example: https://doc-editor.nexusgrcom/plugins/servlet/saml/auth). If the Confluence server is protected by Hybrid Access Gateway (that is, configured as a resource), the values should be as the Confluence server knows itself. It could be an IP address.
-
With these settings, a basic functionality is set up. To do more settings, edit the service provider and go to the Assertion Settings tab.
-
The end user in Confluence can now click Corporate Login on the user login page.
Troubleshooting
-
If a 403 page is shown, investigate the audit log for the Policy Server in Hybrid Access Gateway trying to find out what is wrong.
-
If the page comes back with a red plugin error, look in the system log of the Confluence server.
