Use case in Certificate Manager: Prepare for Card Verifiable Certificate
This article includes updates for CM 8.10.
This article describes the Card Verifiable Certificate (CVC), which is a special certificate type that can be created in Smart ID Certificate Manager (CM).
The CVC is a certificate type used with:
Smart cards in German health control, also called "elektronische Gesundheitskarten"
Machine-readable travel documents and eIDAS tokens, used in German ID cards (Personalausweis) and European passports and driving licenses
The purpose of the CVC is to verify the card itself, and to provide a mutual authentication mechanism between terminal and chip.
Some of the characteristics are:
The CVC contains only a small amount of data
Part of the key and attributes are contained in the signature and/or certificate. This makes it possible to recover this data during authentication.
CM supports CVCs for root CAs, subordinate/intermediate CAs, link CAs and for issuing card-holder or client CVCs. The format of the CVC is identified by the Certificate Profile Identifier (CPI), which is part of the certificate itself. See the "Card Verifiable Certificate (CVC) Formats" chapter in the Technical Description for a list of supported CPIs in CM.
You use Administrator's workbench (AWB) for these tasks.
Prerequisites
See the prerequisites in Create CA key in Certificate Manager and Create CA in Certificate Manager.
Step-by-step instruction
Create root CA for CVC
Start AWB and log in.
Create a CA key as described in Create CA key in Certificate Manager.
For generation 0, the key shall be an RSA key with a length of 1024 bits.
For generation 1, the key shall be an RSA key with a length of 2048 bits.
For generation 2 or 3 (CPI=0x70 or CPI=0x00), the key shall be an ECC key with a length of 256, 384, or 512 bits. SHA-2 must be used as the signature algorithm and its output size must match the key length.
Note: CVC can only use brainpool curves.
Create a CA as described in Create CA in Certificate Manager. Make sure the following values are chosen:
In Authority Name, enter CVC ROOT.
Set State to Active.
In Domain, select Root.
Set Authority type: CA
In Issuing CA - check Self signed
In Usage - check Certificate signing
In Key - select the key created in step 2
In Format - select cvc-ca
Click the browse button and select field CV Certificate Data Elements and deselect all other options in the Fields Chooser dialog.
Click the browse button belonging to CV Certificate Data Elements to open the dialog box.
This dialog is displayed. Enter the values and click OK.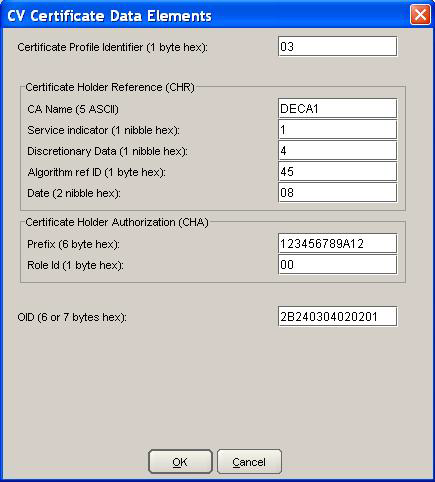
When the root CA has been created, a new CA icon will appear in the Authority Hierarchy. Select or open the new CA in the hierarchy and double-click the certificate icon. The certificate is displayed in a specific dialog box. It is possible to save the certificate and the public key to files.
Create subordinate CAs for CVC
Start AWB and log in.
Follow the instructions as stated in "Create root CA for CVC" above with this exception:
In Issuing CA, select the root CA (do not check Self signed).
Create Link CAs for CVC of type CPI 0x00
There are two options to create a Link CA:
Manually
Follow the instructions in “Create root CA for CVC” above, with these exceptions:
In Format, select cvc-cpi00-linkca. The user has to manually select the CA to be used as Issuing CA by the new Link CA.
Edit the rest of the CVC attributes accordingly in order to create a valid CVC Link CA.
Use Create Link CVCA button
Right-click the Root CV CA that the Link CA will point to, and select Create Link CVCA button.
The Format field will be changed to cvc-cpi00-linkca. The rest of the attributes are copied from the Root CA for convenience.
If needed update the Key and the Signature Algorithm values.
Open the CV Certificate Data Elements, edit the Certificate Holder Reference CVC attributes and increment the Sequence Number. Update any other CVC attribute as needed.
Click OK to create the Link CA.
Create policy procedures for Card Holder (CH) CVCs
Create a certificate procedure as described in Create certificate procedure in Certificate Manager. Make sure to select a CVC CA as Issuing CA and cvc-card as Certificate format. If the issuing CA uses CV certs with CPI=0x70 or 0x00, the Signature algorithm must match that of the CA.
Create a token procedure as described in Create token procedure in Certificate Manager. Make sure to select Storage profile PKCS10.
This step is not required for CV Certificates with CPI=0x00.
All the necessary preparations for CVCs have now been made. Use the CM Software Development Kit (SDK) to issue the certificates.
