This article includes updates for Certificate Manager 8.10.
The Administrator's workbench (AWB) used for the administration of Authorities. Officers with appropriate roles are able to create, configure, and remove the various entities that make up an Authority, such as:
-
Domains
-
Certificates
-
Keys
-
Policies
-
Officers
The AWB user interface is an Explorer style browser where an entity can be selected and its information viewed. You can perform actions on the entities using commands in the menu bar, toolbar or by using shortcut menus.
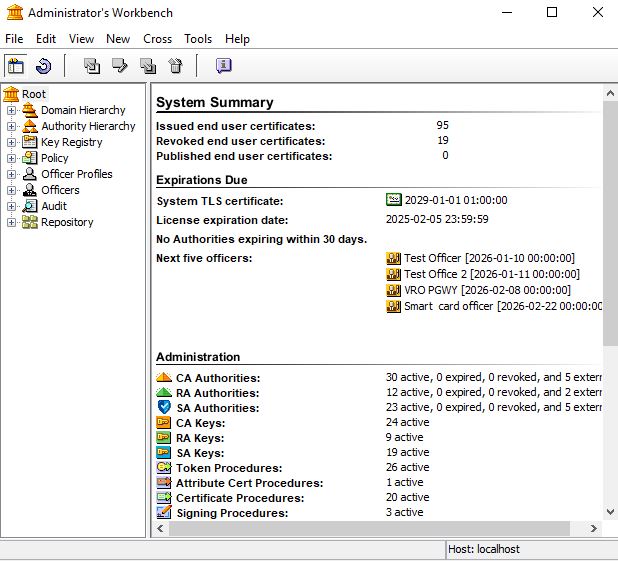
The main window presents:
-
a hierarchical view of the entities in the left-hand pane (explorer bar)
-
information about a selected entity or a system summary in the right-hand pane (information pane)
Some of the functionalities described is only available if the present license enables it. The license is checked when starting AWB. Functions and items related to key archiving and recovery, attribute certificates and card verifiable certificates will only be visible in the GUI when permitted by the license. The signing authority functionality requires a license as well.
These are the CA administration entities:
|
Domain Hierarchy |
Domains can be used to separate hosted tenants in the system by use of access rights per domain, or to group geographically separated regions. The top domain is called Root. In general, officers can only manipulate objects that belong to their own domain or sub domain. Super objects can be used and viewed, but not modified, if they are marked as visible in sub domain. If an object does not have a domain association, it belongs to the Root and it can be referenced from all domains. |
|---|---|
|
Authority Hierarchy |
The Authority Hierarchy group provides access to all the CAs, secondary CAs, RAs and SAs of the system displayed as hierarchical authority chains under the group icon. The root of each authority chain is either a self-signed CA or a CA with an absent signer. |
|
Key Registry |
The Key Registry group provides access to the Authority keys that have been created in the system, organized into three subgroups:
|
|
Policy |
The Policy group provides access to the procedures, rules, and formats used for issuing tokens and end-user certificates with the Authorities. There are several organizational subgroups:
|
|
Officer Profiles |
The Officer Profiles group provides access to the officer profiles created for the system. Officers are assigned roles, which allow them to perform various tasks. Roles are defined in officer profiles and one officer profile has to be selected for each officer created. |
|
Officers |
The Officers group provides access to the officers created for the system. |
|
Audit |
Audit provides access to the audit logs. All significant actions performed by or within the system are logged. Unlike the other groups, all information presented here is strictly read-only. There are no organizational subgroups, only two static entities: CIS log and Request log. |
|
Repository |
Selected entities from the other groups may be organized in folders in the same way as files are organized in a hierarchical file system. This can be useful for collecting all information relevant to a particular authority in a single folder. |
The names of the entities shown in the explorer bar are user-defined. It is recommended to use a logical naming convention.
