This article describes what changes need to be done in Smart ID Digital Access component to mitigate problems and avoid downtime due to the SameSite cookie directive change.
We have now created a resolution for the full problem spectrum with the Samesite directive. As mentioned before, older browsers could not be sent the new directive due to bugs and the fact that the unimplemented feature sometimes breaks current functionality. This has now been resolved with a configuration file placed on the Access Point which will identify the problematic browsers and act accordingly in these cases. The fact that this is a configurable file makes it possible to adapt to future discoveries of the same sort without needing to replace the binaries again.
Note that the first hotfix which was made available on February 11th does not have this full functionality and if applied already it must be replaced with the below version.
Background
In May 2019, Google announced improved cookie security and handling in this draft. The changes proposed in this draft will be adopted into major browsers in February 2020. It is not in the context of this article to describe the reasoning, causes and general effects of this change so please take the time to read this post on the subject. This modification will affect a vast number of systems on the internet and it is likely that many services will have decreased functionality during a period following this change.
Update 2020-04-28: In Safari, on the latest version of iOS (13.4.1), Apple released an update regarding privacy. The browser will now block all third-party cookies, independent from the SameSite configuration.
Time frame
The changes by Chrome were initially scheduled for update 80 scheduled for the 4th of February 2020 but the release has been pushed forward to a small subset on the 17th of February. It is therefore not currently known when the changes will be incorporated in larger proportion of the user base, but it is recommended that the described fix is applied as soon as possible to avoid any downtime or negative user experience.
Implications for Digital Access component
Digital Access component uses two cookies to keep track of the user session: WAAK, which is marked as secure (will only be delivered in an SSL context) and WASID, which is not marked as secure (to be able to track the session over non-SSL contexts).
One of the changes mentioned above is that cookies which are NOT marked as secure will no longer be delivered in an SSL third-party context. This means that the WASID cookie will not have full functionality as before.
In a basic Digital Access component installation, this it not a concern as the user will stay in a first-party context during the entire session. There are however other use cases that will be affected.
Examples of affected use cases:
-
When Digital Access component is embedded in an iframe or similar under a different domain than the main site.
-
SAML federation, when the user will be transported to a different domain for authentication, which will trigger third-party cookie handling.
Available solution: hotfix
The solution, which will fit most contexts, is to start setting the secure flag for the WASID cookie as well as defining it as SameSite=none. This solution will be provided as a hotfix for the Access Point and the process to apply it is quick. For information on the available versions and checksums, see the table below.
Apply hotfix - Step-by-step instruction
The steps to apply the fix are as follow:
-
Log in with your Nexus support account to Nexus' Support Portal via this link: Download Samesite hotfix - HAG-1858.
-
Select your current version of Digital Access component, and download the .zip file. For information on the available versions and checksums, see the table below.
-
Copy the new binary from the .zip file to the appliance, for example by using the secure copy (scp) command. Also copy the supplied configuration file Samesite.conf to the appliance using the same method.
-
Connect via secure shell (ssh) to the Digital Access component appliance.
-
Elevate the prompt:
sudo su -
-
Verify that this system is running a General Available release:
-
Run the following command:
/opt/nexus/access-point/bin/access-point -versionThis command will display something like this:
Name: Access PointVersion: Release 5.13.4, (build 301 - 20191112)where
301is the build number. -
Verify that the build number is a three digit number.
If it's a four digit number it means that this Access Point is already running a different hotfix which will be removed if the new hotfix is applied. If that is the case, contact Nexus support for instructions on how to proceed. See the Contact section below.
-
-
Stop the Access Point:
/etc/init.d/access-point stop
-
Make a backup of the original Access Point file:
cp /opt/nexus/access-point/bin/access-point ~/access-point.old
-
Replace the file. This example assumes that the new binary is available in
/home/agadmin:cp ~/access-point /opt/nexus/access-point/bin/access-point
-
Add the configuration file.
This example assumes that the new file is available in/home/agadmin:cp ~/access-point /opt/nexus/access-point/config/samesite.conf
-
Modify file permissions:
chown pwuser:pwuser /opt/nexus/access-point/config/samesite.conf
-
Start the Access point:
/etc/init.d/access-point start
-
Verify in the developer tools of any browser that both the WAAK and WASID cookies are set with the
Secureflag:
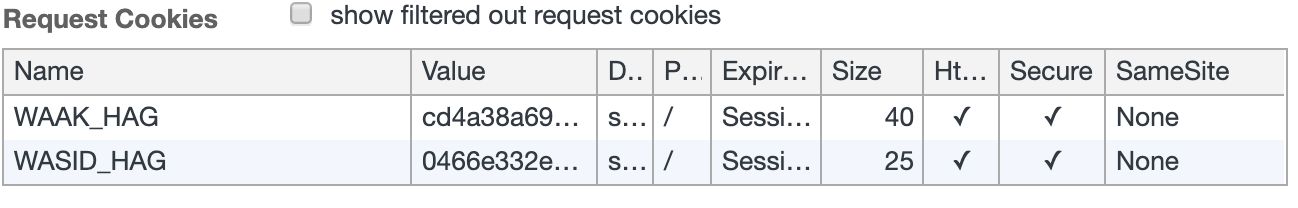
Available versions
The fix is available for the following Digital Access component versions:
|
Version of Digital Access component |
Path to .zip file |
SHA 256 checksum |
|---|---|---|
|
5.12.0 |
./5.12.0/access-point-samesite-5.12.0.zip |
35edd7d7571adb5f66897e9032b572c6b3b2e91233cf2dd9cff8fae00ccbfddf |
|
5.13.0 |
./5.13.0/access-point-samesite-5.13.0.zip |
a050ca36d8e2cc4cbc1f025d5c3ddab97f8214339c6759673038de2e82085d9c |
|
5.13.1 |
./5.13.1/access-point-samesite-5.13.1.zip |
cca22b669be0818ff824d497bdd53ca149b0b2c742cb523e8ea786659f5f299b |
|
5.13.2 |
./5.13.2/access-point-samesite-5.13.2.zip |
7822f3bf694ecf2466b3e8bbb40d04ef9a5c25e2ea36850ecc62e1d8b5783950 |
|
5.13.3 |
./5.13.3/access-point-samesite-5.13.3.zip |
541f96e085a591998ee9883c4e71278a432126dd930dd0e7c96c50ad2ef7d63c |
|
5.13.4 |
./5.13.4/access-point-samesite-5.13.4.zip |
8a8a9ec8cca1310c10e114f8534f12083b4f00ccf8d0dda9adfbebcbcf95fd03 |
|
5.13.5 |
./5.13.5/access-point-samesite-5.13.5.zip |
a03b13c1bbea43a6d0e519c48d4c09e39ddc9a81b5b7fab760028e1ca867d5c4 |
Contact
Please address any questions about the fix and how to apply it to support@nexusgroup.com.
Related information
Links
Download hotfix
You need to have a Nexus support account to access this site.
For more information
